Bitwarden & Qnap & Docker
![]() Posted on Tue 02 June 2020 in Automatyczny dom
• [7 min read]
Posted on Tue 02 June 2020 in Automatyczny dom
• [7 min read]
Będzie po angielsku bo może przyda się światu. ;)
Short instruction how to run Bitwarden service on home Qnap NAS.
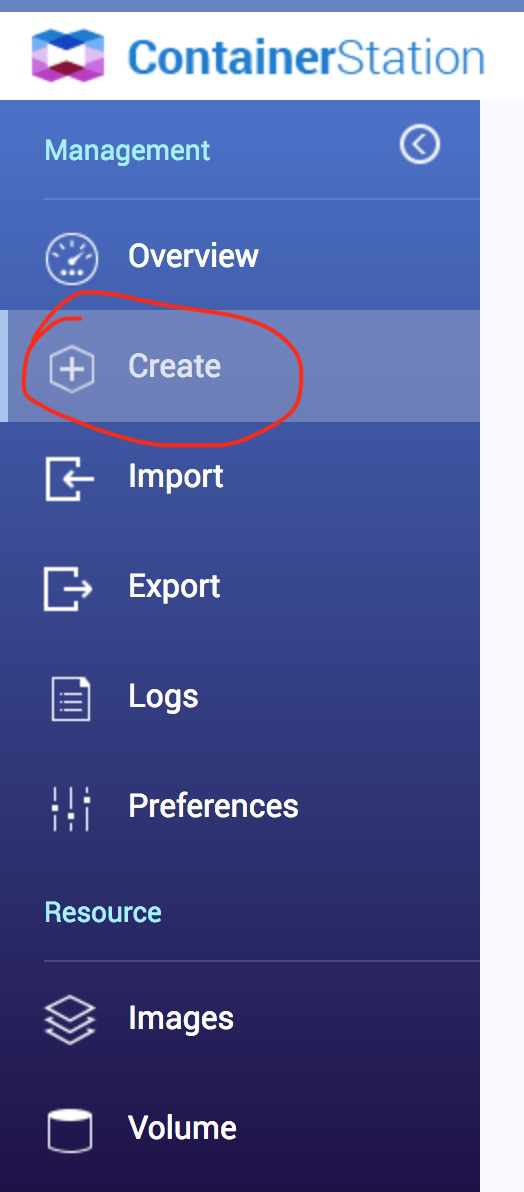
Install "Container Station" on your Qnap. On the left panel of" Container Station" click on "Create" button and then on "Create Application" in upper right corner of window. In the text input field put content of the following listing and name this new application "bitwarden".
version: '3' services: bitwarden: image: bitwardenrs/server:latest expose: - "80" volumes: - ./data/bitwarden:/data restart: on-failure environment: WEBSOCKET_ENABLED: 'true' logging: driver: "json-file" nginx: image: nginx:1.15-alpine ports: - "580:80" - "5443:443" volumes: - ./data/nginx:/etc/nginx - ./data/ssl:/etc/ssl bw_backup: image: bruceforce/bw_backup:latest container_name: bw_backup restart: on-failure depends_on: - bitwarden volumes: - ./data/bitwarden:/data - /etc/timezone:/etc/timezone:ro - /etc/localtime:/etc/localtime:ro - ./data/bitwarden:/backup_folder/ environment: - DB_FILE=/data/db.sqlite3 - BACKUP_FILE=/backup_folder/db_backup/backup.sqlite3 - BACKUP_FILE=/data/db_backup/backup.sqlite3 - CRON_TIME=0 5 * * * - TIMESTAMP=false - UID=0 - GID=0
Accept it and run. What you have really done is Docker Compose YAML configuration file which pulls 3 images from Docker Hub server:
- bitwarden_rs - an unofficial Bitwarden server implemented in Rust language,
- nginx - web server required here as proxy for HTTPS requests,
- bw_backup - a docker image running cron job to backup bitwarden database.
and runs containers of them inside "Container Station".
You should pay particular attention to the ports configuration, line with "580:80" and "5443:443" frases. "580" and "5443" are outside ports which are open on the Qnap itself. You can change to whatever fits for you but don't use 80, 443 or 8080 because they are already taken by Qnap own services.
Before you run freshly created application (that's Qnap Container Station's name for docker-compose GUI) SSH log into Qnap and go to application folder:
cd /share/Container/container-station-data/application/bitwarden/data
Now, you must create configuration for nginx:
events {} http{ server { listen 80; return 301 https://$host$request_uri; } server { listen 443 ssl; ssl_certificate /etc/ssl/certs/bitwarden.crt; ssl_certificate_key /etc/ssl/private/bitwarden.key; location / { proxy_pass http://bitwarden; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; } } }
Save it as nginx.conf to /share/Container/container-station-data/application/bitwarden/data/nginx folder.
Now, you have to create self signed certificate to encrypt HTTP requests with SSL. To do this log in to Qnap with SSH and run following commands:
git clone https://github.com/JulianRunnels/Bitwarden_Self_Host.git
In this repo you'll find two interesting files: data/ssl/bitwarden.ext:
# OpenSSL root CA configuration file. # Copy to `/root/ca/openssl.cnf`. [ ca ] # `man ca` default_ca = CA_default [ CA_default ] # Directory and file locations. dir = ./data/ssl certs = $dir/certs crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # The root key and root certificate. private_key = $dir/private/myCA.key certificate = $dir/certs/myCA.crt # For certificate revocation lists. crlnumber = $dir/crlnumber crl = $dir/crl/ca.crl.pem crl_extensions = crl_ext default_crl_days = 30 # SHA-1 is deprecated, so use SHA-2 instead. default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 375 preserve = no policy = policy_strict [ policy_strict ] # The root CA should only sign intermediate certificates that match. # See the POLICY FORMAT section of `man ca`. countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional [ policy_loose ] # Allow the intermediate CA to sign a more diverse range of certificates. # See the POLICY FORMAT section of the `ca` man page. countryName = optional stateOrProvinceName = optional localityName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional [ req ] # Options for the `req` tool (`man req`). default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only # SHA-1 is deprecated, so use SHA-2 instead. default_md = sha256 # Extension to add when the -x509 option is used. x509_extensions = v3_ca [ req_distinguished_name ] # See <https://en.wikipedia.org/wiki/Certificate_signing_request>. countryName = Country Name (2 letter code) stateOrProvinceName = State or Province Name localityName = Locality Name 0.organizationName = Organization Name organizationalUnitName = Organizational Unit Name commonName = Common Name emailAddress = Email Address # Optionally, specify some defaults. countryName_default = US stateOrProvinceName_default = localityName_default = 0.organizationName_default = organizationalUnitName_default = emailAddress_default = [ v3_ca ] # Extensions for a typical CA (`man x509v3_config`). subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ v3_intermediate_ca ] # Extensions for a typical intermediate CA (`man x509v3_config`). subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ usr_cert ] # Extensions for client certificates (`man x509v3_config`). basicConstraints = CA:FALSE nsCertType = client, email nsComment = "OpenSSL Generated Client Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment extendedKeyUsage = clientAuth, emailProtection [ my_subject_alt_names ] DNS.1 = bitwarden.lan DNS.2 = www.bitwarden.lan [ server_cert ] # Extensions for server certificates (`man x509v3_config`). basicConstraints = CA:FALSE nsCertType = server nsComment = "OpenSSL Generated Server Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = critical, digitalSignature, keyEncipherment extendedKeyUsage = serverAuth subjectAltName = @my_subject_alt_names [ crl_ext ] # Extension for CRLs (`man x509v3_config`). authorityKeyIdentifier=keyid:always [ ocsp ] # Extension for OCSP signing certificates (`man ocsp`). basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning
and script called create_ssl.sh:
#!/bin/bash clear echo "Creating directory structure for CA" mkdir -p data/ssl/certs mkdir -p data/ssl/csr mkdir -p data/ssl/private mkdir -p data/ssl/newcerts touch data/ssl/index.txt echo 1000 > data/ssl/serial clear echo "Creating key for personal CA, please fill out the FQDN with the name you want for your CA" echo "" openssl genrsa -aes256 -out data/ssl/private/myCA.key 4096 chmod 500 data/ssl/private/myCA.key echo "Creating personal CA" echo "" openssl req -config data/ssl/bitwarden.ext -x509 -new -sha256 -days 3650 -extensions v3_ca -key data/ssl/private/myCA.key -out data/ssl/certs/myCA.crt clear echo "Creating key for bitwarden certificate" echo "" openssl genrsa -out data/ssl/private/bitwarden.key 2048 echo "Creating request for Bitwarden certificate, please fill out the FQDN with the nmae that the instance will be located at" echo "" openssl req -config data/ssl/bitwarden.ext -key data/ssl/private/bitwarden.key -new -sha256 -out data/ssl/csr/bitwarden.csr echo "" clear echo -n "Please enter your FQDN for your bitwarden instance: " read answer sed -i "/DNS.1 = */c\DNS.1 = $answer" ./data/ssl/bitwarden.ext sed -i "/DNS.2 = */c\DNS.2 = www.$answer" ./data/ssl/bitwarden.ext openssl ca -config data/ssl/bitwarden.ext -extensions server_cert -days 375 -notext -md sha256 -in data/ssl/csr/bitwarden.csr -out data/ssl/certs/bitwarden.crt echo "" echo "Your personal CA has been created, please make sure to install myCA.crt as a trusted root CA in all devices you want to connect to this instance"
You can edit data/ssl/bitwarden.ext to make cert generating easier. Look at this lines:
# Optionally, specify some defaults. countryName_default = PL stateOrProvinceName_default = mazowieckie localityName_default = Warszawa 0.organizationName_default = FUBAR organizationalUnitName_default = fubarek emailAddress_default = bzzzdet@funar.pl
and this:
[ my_subject_alt_names ] DNS.1 = bitwarden.fubar DNS.2 = www.bitwarden.fubar
Warning: your certificate will be valid only for above domains. I use Pi-hole local DNS to redirect bitwarden.fubar to my QNap IP address.
OK, run create_ssl.sh script and follow instructions. At the and you will find whole new structure of folders with files in ssl directory.
Copy certs and private folders to /share/Container/container-station-data/application/bitwarden/data/ssl.
Now, start Bitwarden application:

Open web browser and go to the URL like: https://bitwarden.fubar:5443, remeber to change domain to same value as in DNS.1 for ssl.
You should see Bitwarden login page:

Time to install and use Bitwarden clients on desktops (macOS, Linux, Windows) and mobiles (Android, iOS) but before you'll do it first go back to SSH session on you Qnap and copy "myCA.crt" file on your computer.
This file is, root CA certificate that will make your Bitwarden clients think that certificate used to connect is valid even it is self signed by you.
Install CA certificate on every host you use with Bitwarden client:
macOS - double click on CRT file and it will open in Keychain Access, add it to System keychain and choose "Always Trust" option,
Linux (Debian/Ubuntu)- https://askubuntu.com/questions/73287/how-do-i-install-a-root-certificate
If your CA is in PEM format convert .pem file to a .crt file:
openssl x509 -in myCA.pem -inform PEM -out myCA.crt
- Create a directory for extra CA certificates in /usr/share/ca-certificates:
sudo mkdir /usr/share/ca-certificates/extra
- Copy server_rootCA.crt file to this directory:
sudo cp myCA.crt /usr/share/ca-certificates/extra/.
- Let Debian/Ubuntu add the .crt file's path relative to /usr/share/ca-certificates to /etc/ca-certificates.conf:
sudo dpkg-reconfigure ca-certificates
3a. To do this non-interactively, run:
sudo update-ca-certificates
Windows - don't use it.
iOS:
In my setup I use local domain name (bitwarden.fubar) when I connect with OpenVPN client from my mobile so, I had to set up additional options to ovpn config file and to OpenVPN server.
First: I already have PiHole server on Raspberry Pi (IP: 192.168.0.10) with option translating "bitwarden.fubar" to IP of my Bitwarden host (say its: 192.168.0.13).
In my ovpn config file add two options:
push "redirect-gateway def1" push "dhcp-option DNS 192.168.0.10"
In my router configuration I use separate DHCP pool for OpenVPN connections. For this pool DNS server to set up to 192.168.0.10). So, when mobile establishes VPN connection all DNS queries are redirected to 192.168.0.10 and it translates "bitwarden.fubar" to 192.168.0.13 which is my Bitwarden instance.
Little bit complicated but... I liked it.
Firefox - go to Preferences -> Privacy & Security -> View Certificates. Click Import, then choose PEM/CRT file, select "Trust this CA to identify websites."
Chrome - in macOS it uses Keychain so you don't need to add it again. For Linux check this website: https://thomas-leister.de/en/how-to-import-ca-root-certificate/. Quick hint: go to Settings -> Privacy & Security -> Security -> Manage Certificates and Import.
Warning! Original Bitwarden Desktop client use chromium sandbox so you HAVE TO install CA certificate into Chromium!!!
When CA certificate is in right place the last thing is:
before you connect every Bitwarden client must "know" the right address of Bitwarden server.
Run client and click gear icon:

then put your server address in 4 fields:
- Server URL
- Web vault server URL
- API server URL
- Identity server URL
Remember to put it in the following form: https://my.ip.address:myport, in case your server has IP 10.0.0.1 and port 5443 it should be: https://10.0.0.1:5443 like in image below. If you use domain name (as me) you should replace IP with domain:

Now, there's time to create account, you can do it pointing browser to the very same URL as used above: https://10.0.0.1:5443.
It's all now ready to use.
Few steps to consider:
- store database backup somewhere outside Qnap,
- import data from another password manager,
- set up VPN connection to Qnap to synchronize database when you outside.
UPDATE:
How to update docker images?
ALWAYS MAKE BACKUP OF YOUR VAULT!!! Export it in JSON from Bitwarden client.
go to your QNap, run FileStation and zip full content of you application data folder:
stop application in ContainerStation, remove it. Go to Images tab and pull new version of images: bitwardenrs/server, bruceforce/bw_backup and nginx:1.15-alpine.
create application as written at the beginnign of this article, don't run it
unzip content of previously backup data folder (configuration for nginx, ssl, vault and vault's backup).
run application.
